In order to configure new logging you need to go into System –> Logging. By default the following errors are logged:
Logs can be sent to the following Actions (Locations):
Disk
When the disk option is selected then logs are stored on the local hard disk. The local hard disk is around 61MB in size with around 31MB free (This can be viewed by going to System –> Resources). You can amend the log to local hard disk options by clicking it and changing the required parameters:
Echo
Not too sure what Echo is but I’m assuming it echo’s the log to the CLI. Anyways, the following options can be changed for echo:
Memory
Memory refers to the flash memory of the device. This is roughly around 60MB with 45MB spare (This can be viewed by going to System –> Resources). You can also change how many log lines are stored in memory to store more data:
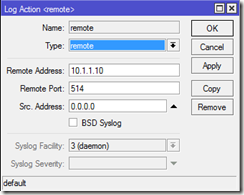
Remote
The final option is remote. This refers to a remote syslog server where you can configure the IP address and port number:
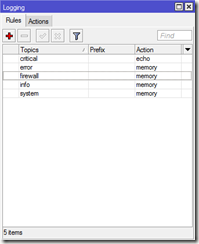
You can log a variety topics which include firewall, account, info, email, dhcp etc etc. I wanted to log all firewall traffic that was being blocked. To do this simply go back to the logging option and click the Red Plus sign under the Rules tab:
In the Topic section add Firewall and then select where you want to log the data to. In my case I’m just logging to memory. You can also prefix some text to all firewall entries so you can easily identify it if you want. Once finished simply click Apply:
Your new rule to log firewall traffic should be visible:
In order for the firewall to start logging traffic you need to add a firewall rule to tell it to log traffic. To add the rule simply click IP –> Firewall and set focus to the Filter Rules tab. By default there are 4 rules in place. The first rule allows ICMP (Ping) traffic on all interfaces. The second and third rules allow established and related traffic and the final rule blocks everything else:
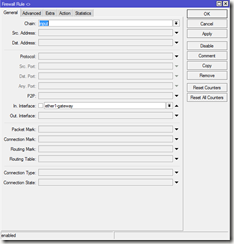
To add a log rule simply click on the red plus to add a new rule. Click on the General tab and set the Chain to be forward and the In. Interface to be your external gateway (Where the internet is connected to):
Click on the Action tab and set the Action to be Log and then also set a log prefix if you want and then click Apply
The new rule should appear in the list of rules. Simply drag the rule to where you want it to take affect. If you want to see all traffic including allowed traffic then drag the rule to the top of the list. If you only want to see dropped traffic then drag it just above the drop rule:
To see if in action click on the Log button and you should dropped traffic starting to appear.










No comments:
Post a Comment